Rooting
Rooting (i.e., modifying the OS so that you can run commands as the root user) is recommended for testing on a real device. This gives you full control over the operating system and allows you to bypass restrictions such as app sandboxing. These privileges in turn allow you to use techniques like code injection and function hooking more easily.
Note that rooting is risky, and three main consequences need to be clarified before you proceed. Rooting can have the following negative effects:- voiding the device warranty (always check the manufacturer's policy before taking any action)
- "bricking" the device, i.e., rendering it inoperable and unusable
- creating additional security risks (because built-in exploit mitigations are often removed)
You should not root a personal device that you store your private information on. We recommend getting a cheap, dedicated test device instead. Many older devices, such as Google's Nexus series, can run the newest Android versions and are perfectly fine for testing.
Which Mobiles Can Be Rooted
Virtually any Android mobile can be rooted. Commercial versions of Android OS (which are Linux OS evolutions at the kernel level) are optimized for the mobile world. Some features have been removed or disabled for these versions, for example, non-privileged users' ability to become the 'root' user (who has elevated privileges). Rooting a phone means allowing users to become the root user, e.g., adding a standard Linux executable called su, which is used to change to another user account.
To root a mobile device, first, unlock its bootloader. The unlocking procedure depends on the device manufacturer. However, for practical reasons, rooting some mobile devices is more popular than rooting others, particularly when it comes to security testing: devices created by Google and manufactured by companies like Samsung, LG, and Motorola are among the most popular, particularly because they are used by many developers. The device warranty is not nullified when the bootloader is unlocked and Google provides many tools to support the root itself. A curated list of guides for rooting all major brand devices is posted on the XDA forums.
Rooting with Magisk
Magisk ("Magic Mask") is one way to root your Android device. Its specialty lies in the way the modifications on the system are performed. While other rooting tools alter the actual data on the system partition, Magisk does not (which is called "systemless"). This enables a way to hide the modifications from root-sensitive applications (e.g. for banking or games) and allows using the official Android OTA upgrades without the need to unroot the device beforehand.
You can get familiar with Magisk by reading the official documentation on GitHub. If you don't have Magisk installed, you can find installation instructions in the documentation. If you use an official Android version and plan to upgrade it, Magisk provides a tutorial on GitHub.
Furthermore, developers can use the power of Magisk to create custom modules and submit them to the official Magisk Modules repository. Submitted modules can then be installed inside the Magisk Manager application. One of these installable modules is a systemless version of the famous Xposed Framework (available for SDK versions up to 27).
Android Malware
A malicious App / Malware is a software or piece of code designed for nefarious purposes. As practice shows us, these purposes can range from recon (i.e., gathering intel on a designated target to track movement and identify vulnerabilities) to intentionally damage tangible or intangible assets.
Android malware can be characterized in different ways: a systematic characterization is proposed ranging from their installation, activation, to the carried malicious payloads. Thus, malware installation can be generalized into three main social engineering-based techniques:
-
Repackaging
Repackaging is one of the most common techniques that malware authors use to piggyback malicious payloads into applications. In essence, malware authors get an application file, disassemble them, enclose malicious payloads, reassemble, and submit the new application to an official or alternative market. Users could be vulnerable by being enticed to download and install these infected applications.
-
Update attack
In the case of the update attack, instead of enclosing the payload as a whole only an update component is included, which will fetch or download the malicious payloads at runtime. Because the malicious payload is in the “updated” application, not the original application itself, it is stealthier than the malware installation technique that directly includes the entire malicious payload in the first place.
-
Drive-by download
This technique applies the traditional drive-by download attack to mobile space. Though they are not directly exploiting mobile browser vulnerabilities, they are essentially enticing users to download “interesting” or “feature-rich” applications.
Android Malware Detection
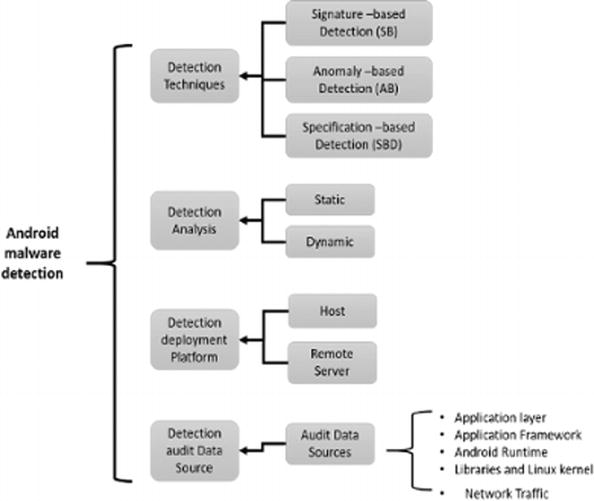
Android Malware Detection techniques can be classified into three detection techniques:
signature-based (SB), anomaly-based (AB), and specification-based (SPB) detection.
Signature-based detection refers to the malware detection by comparing the application signature or pattern captured with a database of known attacks or threats.
Anomaly Based detection monitors regular activities in the devices and looks for any behavior that deviates from the normal pattern.
SPB detection also monitors for any deviation but rather than detecting the occurrence of specific attack patterns; it monitors for deviation of their behavior from the normal specification.
The detection analysis category involves reverse engineering techniques aimed to obtain information about the behavior of a malware in its environment. On the one hand, in static analysis, detection is done through the source code, binary, or the API level without the execution of the Android malware. On the other hand, dynamic detection detects malware through the execution behavior of the malware. In this case, the detection is done through monitoring the execution of Android malware activity at runtime.
The detection deployment platform category helps to identify whether the malware detection is deployed in the host or on a remote server. In host detection, all the activity of the device is monitored, analyzed, and processed in the device itself. Meanwhile remote deployment requires a remote server, which monitors the activity of the device on the device but performs the analysis and detection process on the remote server.
Nowadays, most detection techniques for Android malware use statically extracted data from the AndroidManifest.xml file or Android API function calls, as well as dynamically obtained information from network traffic and system call tracing. Moreover, most current detection systems equipped with a database of regular expressions that specify byte or instruction sequences that are considered malicious are largely based on syntactic signatures and employ static analysis techniques. Unfortunately, static and signature-based analysis techniques can be evaded by malware applications using techniques, such as polymorphism, metamorphism, and dynamic code loading.
List of Tools and their functions for Security Analysis
- Online Analyser
- Static Analysis
- Reverse Engineering
- Dynamic Analysis Tools
- Misc Tools
Online Analyzer Tools
-
Appknox is a Paid platform. It use world's most Powerful plug and play VAPT platform which helps Businesses to build a safe and secure mobile ecosystem. It’s offer Static Application Security Testing (SAST) , Dynamic Application Security Testing (DAST) and API Security testing.
-
VirusTotal is a free service that analyzes files and URLs for viruses, worms, trojans and other kinds of malicious content. VirusTotal inspects items with over 70 antivirus scanners and URL/domain blacklisting services, in addition to a myriad of tools to extract signals from the studied content. Any user can select a file from their computer using their browser and send it to VirusTotal.
-
AppCritique AVA is a vulnerability reporting service that puts mobile apps through dozens of checks, including some of the latest detectable vulnerabilities. By providing detailed security reports within days, it frees app developers to better concentrate on delivering in-demand features and capabilities that take full advantage of iOS and Android’s latest functionality.
-
App Detonator: Detonate APK binary to provide source code level details including app author, signature, build and manifest information. 3 Analysis/day free quota.
-
NowSecure: Enterprise tool for mobile app security testing both Android and iOS mobile apps. Lab Automated features dynamic and static analysis on real devices in the cloud to return results in minutes. Its available in paid version only.
Static Analysis Tools
-
ApkAnalyser is a static, virtual analysis tool for examining and validating the development work of your Android app. It's a complete tool chain which supports modification of the binary application with more printouts. You are then able to repack, install, run and verify the result from logcat. ApkAnalyser also supports resource analysis, and you can decode XML, look up resource references and detect potential issues in your app.
-
APK Inspector is a powerful GUI tool for analysts to analyze the Android applications.
-
JEB Decompiler: Paid JEB is a modular reverse engineering platform for professionals. Perform disassembly, decompilation, debugging, and analysis of code and document files, manually or as part of an analysis pipeline. Use JEB to analyze Android apps, reverse engineer Windows malware, audit embedded code, and much more.
-
StaCoAn: Cross Platform tool which aids developers, bug bounty hunters and ethical hackers performing static code analysis on mobile applications. This tool was created with a big focus on usability and graphical guidance in the user interface.
-
PScout: A version-independent tool to extract the permission specification and take the first steps to an-swer some key questions about Android’s permission system.One of the challenges with extracting a permission specifi-cation from Android is that the permission checks and APIcalls that lead to them are distributed over an extremely large code base.
Reverse Engineering Tools
-
Apktool: A tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original form and rebuild them after making some modifications. It also makes working with an app easier because of the project like file structure and automation of some repetitive tasks like building apk, etc.
-
Dex2Jar: Tools to work with android .dex and java .class files. The core feature of Dex2Jar is to convert the classes. dex file of an APK to classes. jar or vice versa. So, it is possible to view the source code of an Android application using any Java decompiler, and it is completely readable.
-
Android Framework for Exploitation, is a framework for exploiting android based devices and applications.
-
Smali/Baksmali is an assembler/disassembler for the dex format used by dalvik, Android's Java VM implementation. The syntax is loosely based on Jasmin's/dedexer's syntax, and supports the full functionality of the dex format (annotations, debug info, line info, etc).
-
JD-GUI is a standalone graphical utility that displays Java source codes of “.class” files. You can browse the reconstructed source code with the JD-GUI for instant access to methods and fields.
Dynamic Analysis Tools
-
MobSF: Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis. MobSF support mobile app binaries (APK, XAPK, IPA & APPX) along with zipped source code and provides REST APIs for seamless integration with your CI/CD or DevSecOps pipeline.The Dynamic Analyzer helps you to perform runtime security assessment and interactive instrumented testing.
-
AppUse is a VM (Virtual Machine) developed by AppSec Labs. It is a unique platform for mobile application security testing, Android and iOS applications and includes exclusive custom-made tools and scripts created by AppSec Labs.
-
Appie is a software package that has been pre-configured to function as an Android Pentesting Environment. It is completely portable and can be carried on USB stick or smartphone. This is a one stop answer for all the tools needed in Android Application Security Assessment and an awesome alternative to existing virtual machines.
-
AndroidHooker is an open source project for dynamic analyses of Android applications. This project provides various tools and applications that can be used to automatically intercept and modify any API calls made by a targeted application.
-
ARTist is a flexible open source instrumentation and hybrid analysis framework for Android apps and Android’s Java middleware. It is based on the Android Runtime’s (ART) compiler and modifies code during on-device compilation. ARTist blends particularly well into the Android app install mechanism because it does not change the app’s package (APK) file but just replaces the compiled native version, hence it preserves the package signature so that modified apps still receive updates.
Misc Tools
-
Android Debug Bridge (adb): Android Debug Bridge (adb) is a versatile command-line tool that lets you communicate with a device. The adb command facilitates a variety of device actions, such as installing and debugging apps, and it provides access to a Unix shell that you can use to run a variety of commands on a device.
-
AppMon: AppMon is an automated framework for monitoring and tampering system API calls of native macOS, iOS and android apps. It is based on Frida.
-
Android Mobile Device Hardening: AMDH scans and harden device's settings and list harmful installed Apps based on permissions.
-
QARK: QARK by LinkedIn is for app developers to scan app for security issues.
-
Oversecured: A mobile app vulnerability scanner, designed for security researchers and bug bounty hackers. It also allows integrations into the DevOps process for businesses.